I have a ton of virtual machines running on VMWare ESXi servers at home. To access them, I had been logging into the ESXi server and opening a remote console with VMWare Workstation Player. Works great…but it’s a hassle…then I found Apache Guacamole.
Apache Guacamole is a clientless remote desktop gateway. It supports VNC, RDP and SSH. It works in the browser thanks to HTML5 so no agents on the remote side as well…just a web browser. It’s really making bouncing between machines.
I installed Guacamole on a Kubernetes cluster I recently stood up. Simple install. I might turn it into it’s own server at some point, but this was an easy way to get started.
Now that I have a remote gateway, I need some sort of server to run on the clients – originally I intended to use RDP for Windows and VNC for Linux.
RDP on Windows is simple. Enable remote access, configure Guacamole with the IP, username, password, etc. Ready to go.
Now for Linux. All of the documentation/guides for VNC seemed horribly out of date…and a COMPLETE PAIN to get working on Linux. I spent a long time scouring the internet for any recent guides…then figured out why I couldn’t find any information on VNC…it sucks. No one uses it.
Once I found xrdp, the clouds parted and the angels sang. It’s so easy to use.
Installing xrdp
Most of the linux distributions I use are based on Debian. On RHEL/CentOS sub yum for apt-get
sudo apt-get install xrdp
sudo systemctl start xdrp
sudo systemctl enable xrdp
sudo ufw allow 3389/tcpColord Authorization and The Impending Crash Message
One gotcha, which I only see on Ubuntu so far is that when you log in you are prompted to sign in to authorize the color management of the session. This is frustrating…and sometimes the popup doesn’t disappear and a reboot is needed to get rid of it…which it might not go away next time you log in either.
I started to look into how to fix this. I found a great post from c-nergy.
Authorizing colord with PolKit
The PolicyKit Authorization Framework, or polkit, is an authorization system that allows certain users to run certain actions on the system. By default, colord (used in xRDP) is restricted to the root user.
So the first part of the fix, is to allow all users to run colord.
Create the following file: /etc/polkit-1/localauthority.conf.d/02-allow-colord.conf
Add the following code:
polkit.addRule(function(action, subject) {
if ((action.id == “org.freedesktop.color-manager.create-device” ||
action.id == “org.freedesktop.color-manager.create-profile” ||
action.id == “org.freedesktop.color-manager.delete-device” ||
action.id == “org.freedesktop.color-manager.delete-profile” ||
action.id == “org.freedesktop.color-manager.modify-device” ||
action.id == “org.freedesktop.color-manager.modify-profile”) &&
subject.isInGroup(“{users}”)) {
return polkit.Result.YES;
}
});You can be more secure and restrict the group allowed to run colord by changing users in the above snippet to the group you’d like.
System Crash
Unfortunately, this causes a system crash whenever you log in to the Ubuntu system. It seems to be related to polkit and the file we just created – if you remove that file the authorization popups return…but no system crash. So how do we fix this crash?
If you have a polkit version < 0.106 you’ll need to create a .pkla file. To check this, run pkaction --version
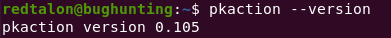
So in my case, I’ll be making a .pkla file. Otherwise make a .conf file.
Create a file /etc/polkit-1/localauthority/50-local.d/45-allow-colord.pkla
Copy/paste the following
[Allow Colord all Users]
Identity=unix-user:*
Action=org.freedesktop.color-manager.create-device;org.freedesktop.color-manager.create-profile;org.freedesktop.color-manager.delete-device;org.freedesktop.color-manager.delete-profile;org.freedesktop.color-manager.modify-device;org.freedesktop.color-manager.modify-profile
ResultAny=no
ResultInactive=no
ResultActive=yesFinally, clear out any previous system crashes
sudo rm /var/crash/*And reboot the system. You should now be able to log in without any authorization prompts or system crash messages.
Recent Comments